Fingerprinting with FOCA
In this lab we will see how to do file fingerprinting using FOCA.

On this occasion we are going to do a scan with the tool called FOCA (Fingerprinting Organizations with Collected Archives).
For this practice I will use www.globant.com as the initial target to learn a bit about FOCA and its use. Then we will use some other target to see cases where there is metadata exposed.
Basic use of FOCA
As a first step we configure the project and the domain target:
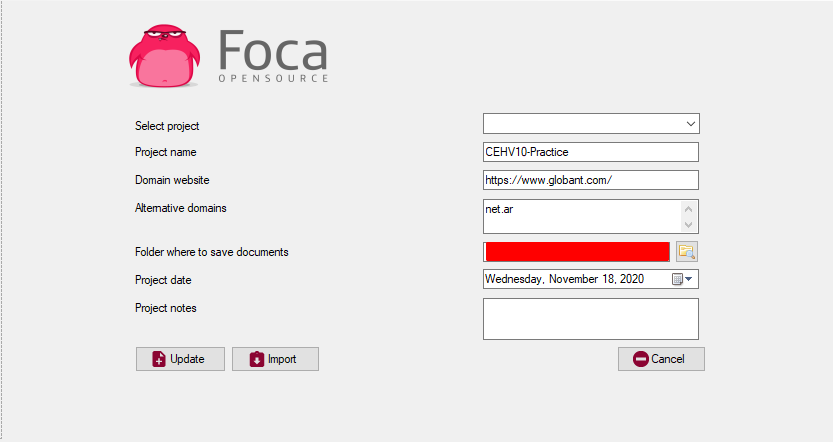
Once ready, we select the file extensions that we want to be taken into account by FOCA when performing the scan:
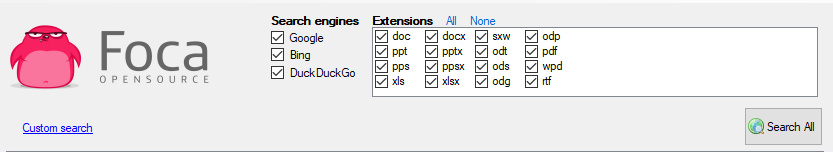
Once ready, we click on Search All to start the scan. Once FOCA it starts detecting files we see them listed below the selection of file extensions:
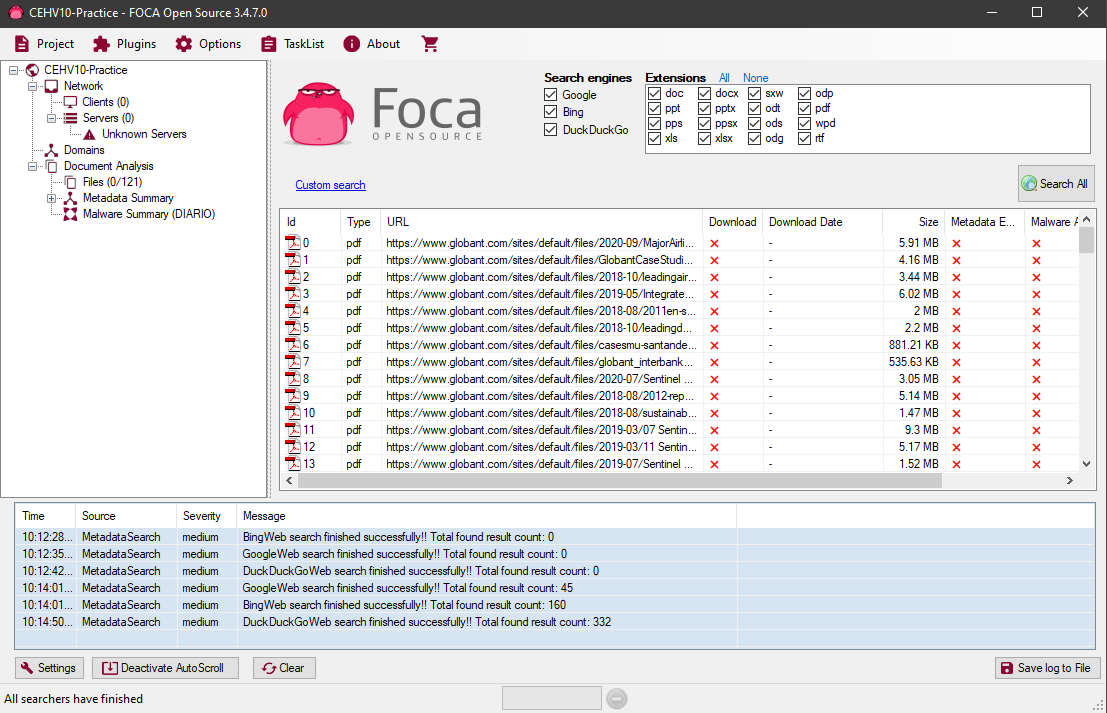
Once we have results available, we can right-click on any of the listed files and give it click on Download to download it and see what information we can obtain from it:
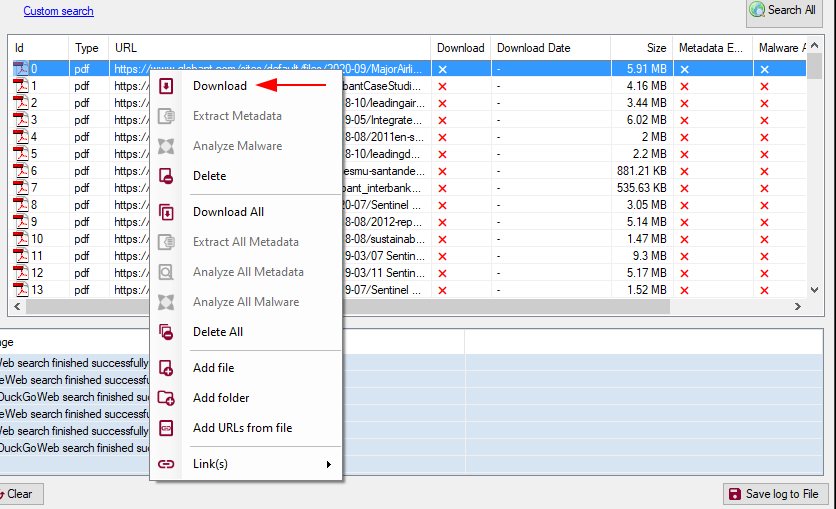
Once the document is downloaded it appears listed in the tree view and we can observe some details about it.
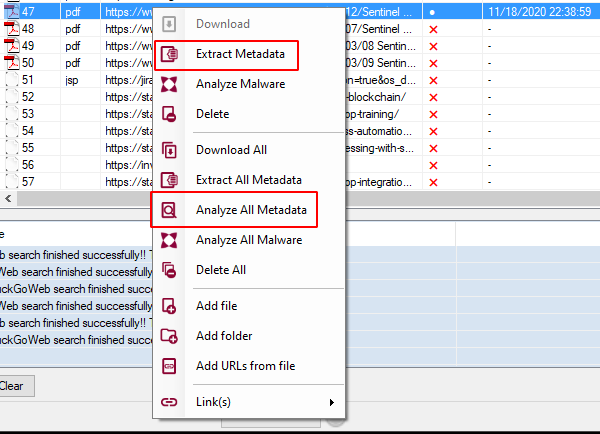
To see the details of the metadata of the file we need to return to the file list and then right-click to the desired file and click on Extract All metadata and then Analyze all metadata.
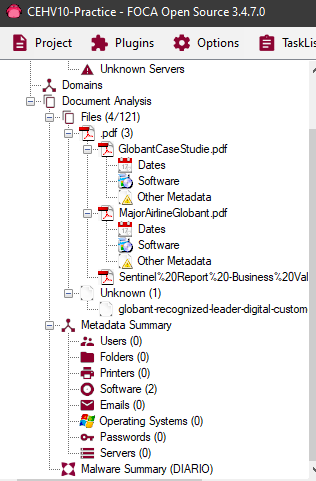
In this case we do not obtain important information since these documents were already sanitized before being published. But in case some important detail is obtained from the metadata of them, FOCA it will list the different types of information in the tree view so that we can review them:
Analysis of Exposed Metadata with FOCA
If we see an example of a file that does expose certain data in its metadata we will see how this information is presented in FOCA:
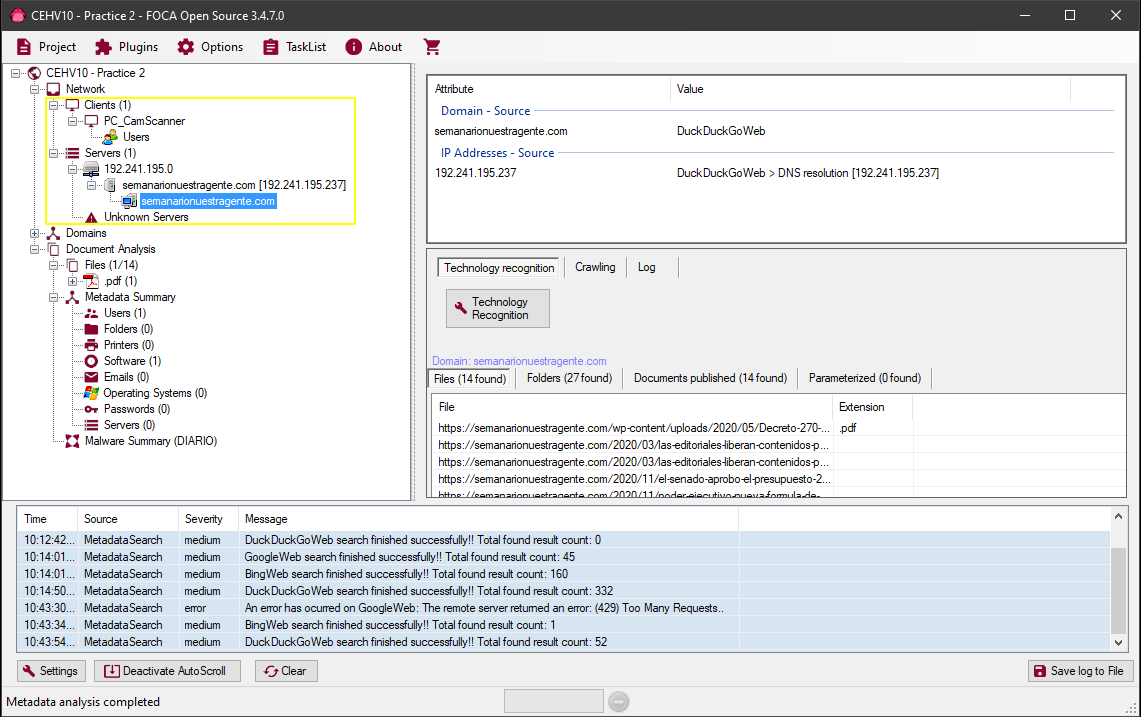
We see that among the results we obtain:
The server's IP address
The Software used to create the File
The User used when creating the file
Each scanned file can expose different pieces of information that allow us to obtain a more complete picture of the target during the reconnaissance phase.
In this other example we see that a PDF from the UTN campus reveals different details when analyzed:
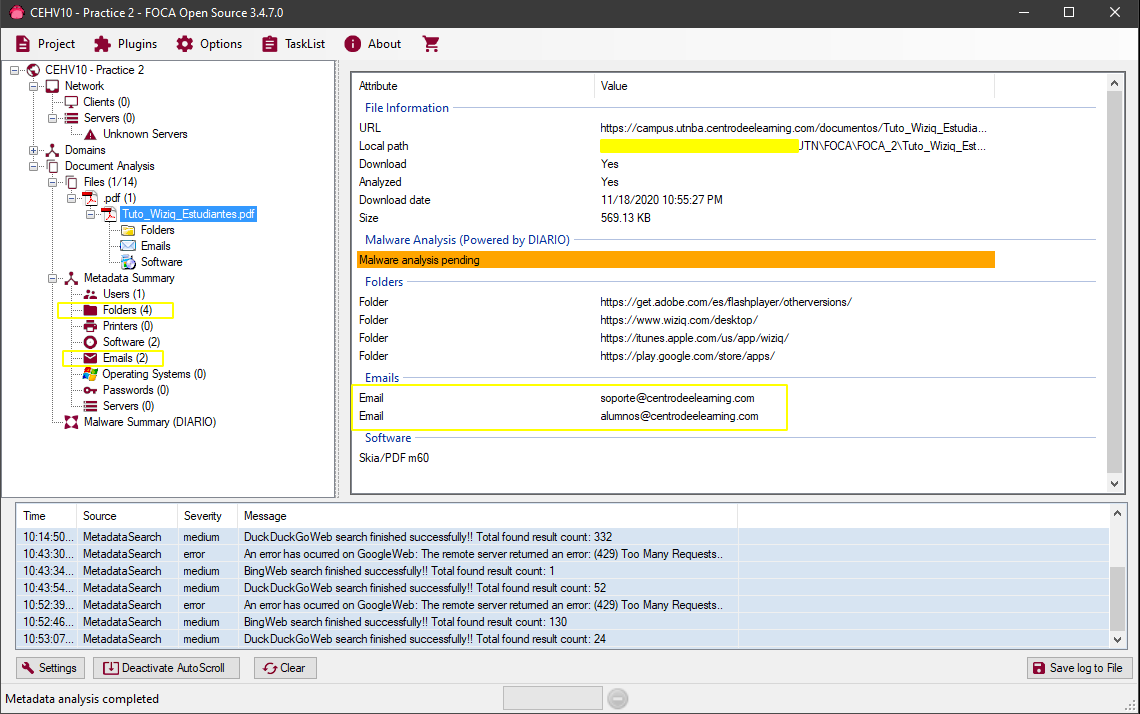
In this case we obtain some folders(Folders), some emails and the version of the software used in the creation of the document.
Some documents reveal much more information:
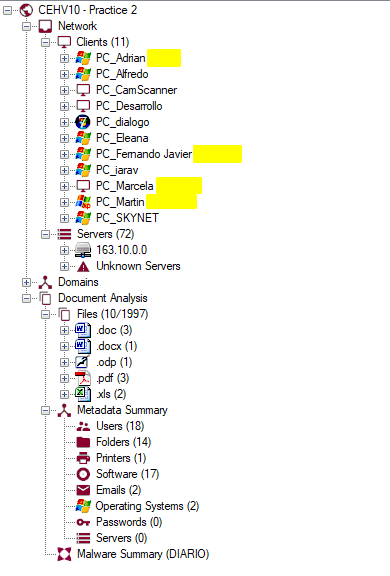
In this case we can see that the metadata extracted from certain documents expose user accounts, emails, printers, folders, even other servers. Clearly sanitizing documents before sharing them is key to preventing external agents from obtaining potentially sensitive details with tools like FOCA.
Last updated
Was this helpful?